
Cybersecurity refers to the practice of protecting computer systems, networks, and data from unauthorized access, use, disclosure, disruption, modification, or destruction. In the digital age, where technology is deeply integrated into our personal and professional lives, cybersecurity has become a critical concern for individuals, organizations, and governments alike.
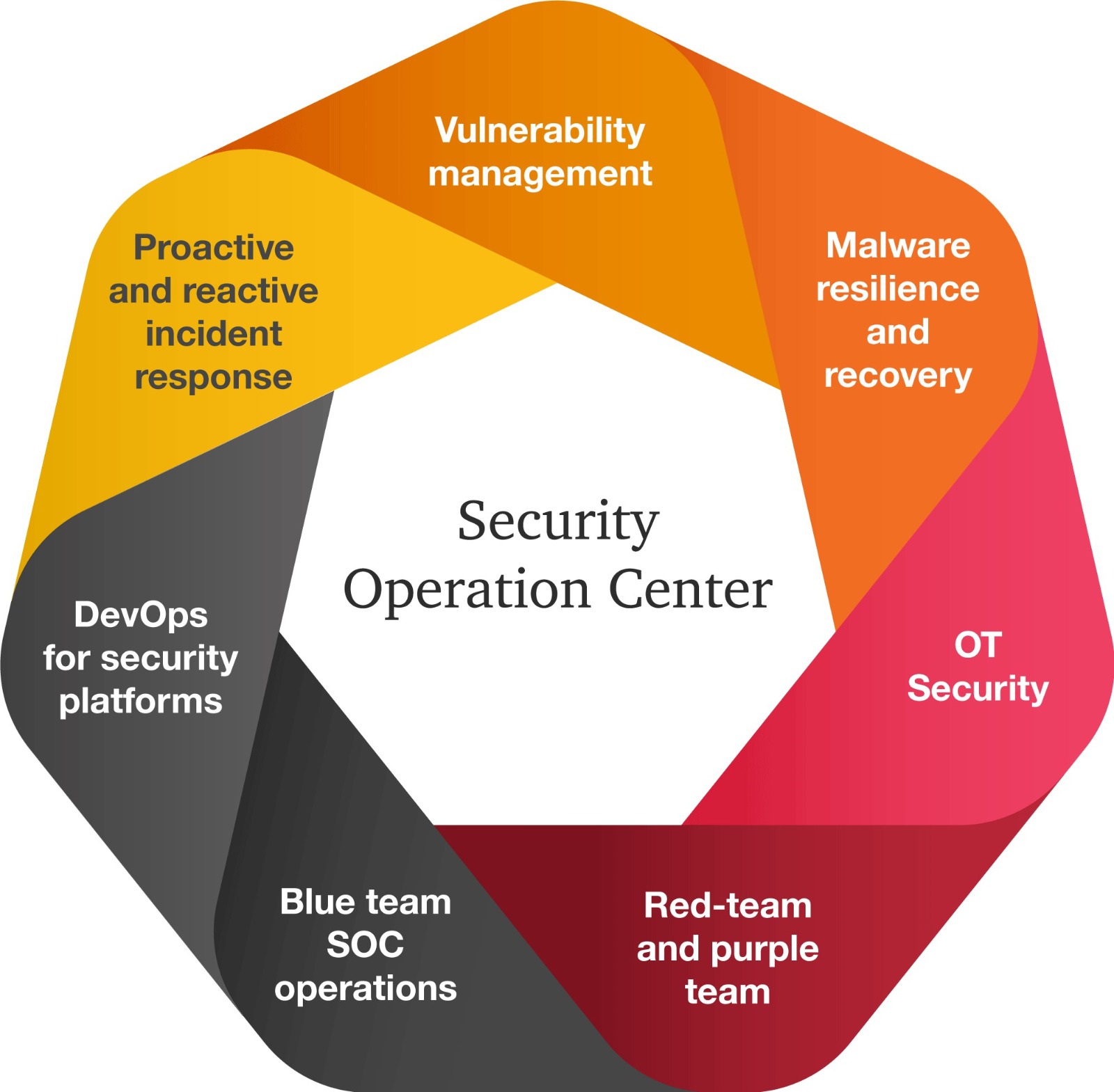

Continuous Monitoring: MDR services monitor an organization’s network and assets 24/7, allowing for early detection of security breaches and minimizing attackers’ dwell time in the network.









Cyber Security
Network Security
Data Center Services
Managed IT Services
Enterprise Solutions
Cloud Services
2023 © All Rights Reserved. Cynetsoft